Information Flow Control
Information flow determines Information security.
(End-to-end) Confidentiality no leakage, no insecure information flow
Integrity data only changed when authorized
Until now we used different security mechanisms.
Problem of security mechanisms:
- None offer full security or end-to-end security
- each have their own weaknesses
- Software is always viewed as black box.
Solution: language-based approach
(Ideally automatic) formal methods for proof of security.
Proofs based on code semantics - security type checking (statically and dynamically)
- controlling information flow
- not being too restrictive (declassifying when necessary)
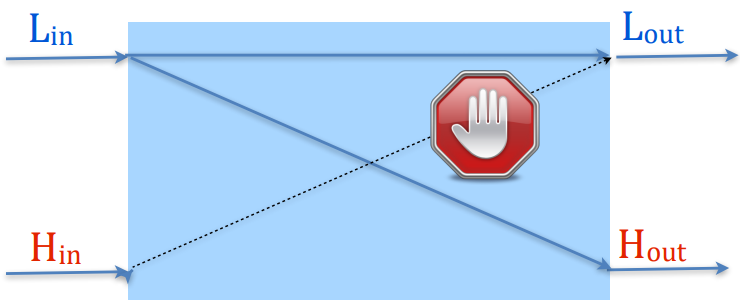
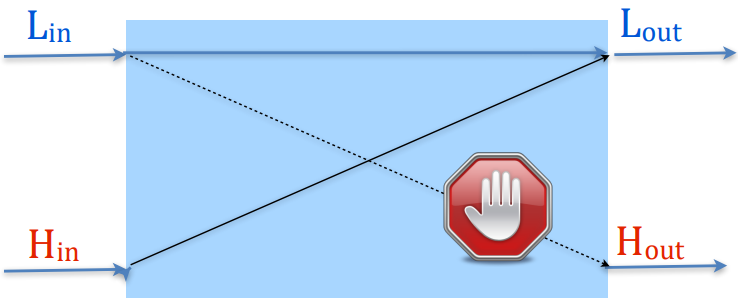
Side channels
Mechanisms to get sensitive information through the observable behaviour of a computing system.
Explicit flow information leakage through direct assignment.
Implicit flow control structure of the program. (Using as a guard)
Termination channels termination / non-termination.
Timing channels execution time of program, cache access time,
Probabilistic channels different stochastic properties, observing behaviour of execution scheduler
Power channels Power consumption by computer
Resource exhaustion c. exhaustion of a finite, shared resource: memory space,
Confidentiality, Integrity
Informal definition of Non-Interference
Non interference = formal definition of confidentiality.
Program is secure if high inputs do not interfere with low inputs.
Computation , with semantics (maps the input to the output or does not terminate )
where
means low memory equality
means low view indistinguishability by attacker
Confidentiality vs. Integrity are dual
Security Types, Security Lattice
Multiple security types: One for confidentiality, one for integrity
High confidentiality means low integrity - vice versa.
confidentiality level integrity level
Formal definition of non-interference
Program satisfies non-interference, if:
wheremeans thatandare equivalent at levelor lower.
This definition is incomplete:
- termination, timing-insensitive
- does not work with multi-threading, non-determinism
Considering Termination
If they do terminate, then they must have the same lower part.
Security Type System
non-interference definition contains a universal quantification over all possible inputs → undecidable.
Static analysis
We type expressions and then enforce rules.
Good option but incomplete because of undecidability.
Insecure program might get accepted.
Description of used notation
We write the preconditions for above the line:
(Security) Types
Simple lattice (there could theoretically be more Types betweenand)
Function that assigns types to variables ("typing environment")
Program counter (as security type)
Judgement: expressionis well typed in
Judgement: programis well typed inand
("join") - like Max function for upper bounds
Assigned type
Type of as assigned by
program counter
always has the higher type:
Explicit flow, impicit flow
If expression has type then:
must be lower than the type of . (implicit flow throughand explicit flow through)
Number— skip instruction — sequencing instructions
Declassification
Sometimes necessary to allow explicit flow ie. for checking passwords. We do not check anymore.
Considering Timing: hiding timing leaks
Cross-copy low slices = dummy instructions (like skip sequences) in each branch that so that both take an equal amount of time - means number of instructions per branch must be equal.
The guard must be low and the entire instruction must be checked under a low . We don't want different looping times based on the guard.