Other exams
Buffer Overflow
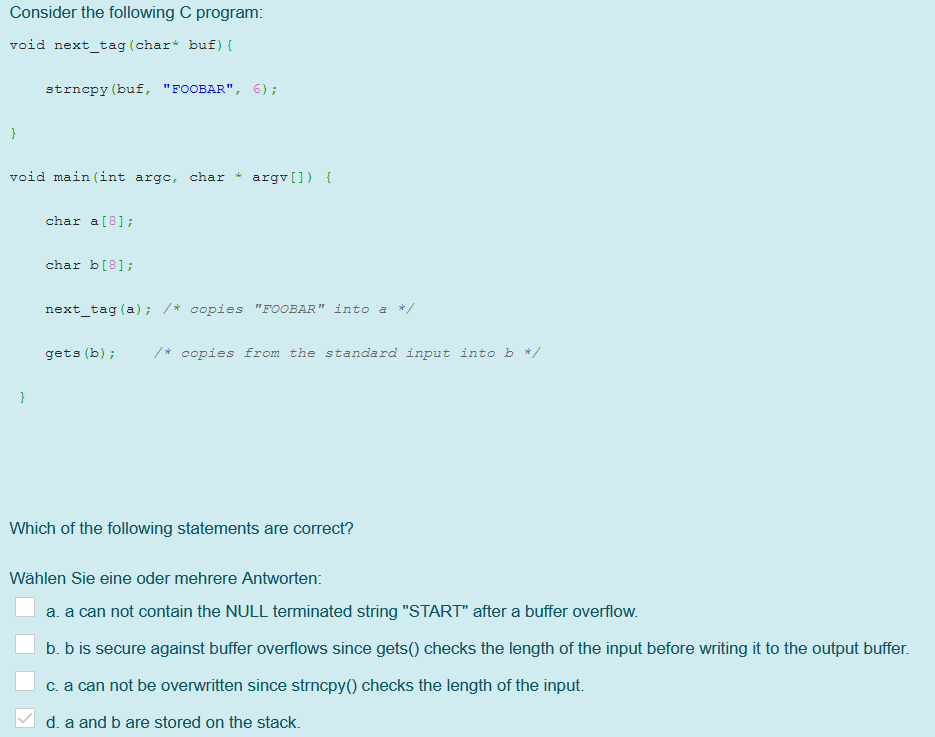
void next_tag(char* buf) {
strncpy(buf, "FOOBAR", 6);
}void main (int argc, char* argv[]) {
char a[8];
char b[8];
next_tag(a) ; /*copies "FOOBAR" into a */
gets(b); /*copies from the standard input into b */
}acan not contain the NULL terminated string "START" after a buffer overflow
bis secure against buffer overflows, sincegets()checks the length of the input before writing it to the output buffer.
acan not be overwritten sincestrncpy()checks the length of the input
aandbare stored on the stack
Solution
-
❌ we can overwrite
ato contain"START\n"When we get access to
band can put in our payload, the local variableacontains the characters"FOOBAR\n"(that means there is 1 free byte ina).
-
❌
gets()does not check boundaries
-
❌
acould be overwritten fromb
- ✅ because they are local variables
-
❌ we can overwrite