Security
Definition
Security
"Strategien, Vorkehrungen und Tools zur gewährleistung von Security-Objectives bei Daten und Services einer Organisation."
Design Principles
Open design Avoid security by obscurity, system should be secure even if open source
Least privilege (= authority to access a resource) for every component and user
Simplicity (= Economy of Mechanisms) easier to analyze
Usability (= acceptability) secure mechanisms must be easy to use
Complete Mediation impossible to bypass access enforcement mechanisms
Cryptography
In geschlossenen Systemen: (theoretisch fehlerfreies) Betriebssystem kann Sender und Empfänger von interprocess communication IPC kontrollieren.
In offenen Systemen notwendig.
Goal vs. Threat
Security Objectives (CIA-Triad)
Confidentiality Secrecy, read-access only to authorized users
Integrity Data only modified when authorized / System behaves as expected
Availability of data and services
Threat
Vulnerability of that can be exploited. If carried out it is an attack.
passive intercepting without affecting system
active modifying data, interrupting service
insider from someone inside the security perimeter
outsider from outsider, unauthorized user
Interception unauthorized read-access
Modification modification or generation of data, Theft of Service (unauthorized usage)
Interruption of a Service through destruction, overloading, ...
Goal Vulnerability Threat
Confidentiality Leaky Exposure / Interception (passive)
Integrity Corrupted Modification / Fabrication (active)
Availability Unavailable Denial of Service / Interruption (active)
Attacks
Attacker / Intruder / Adversary
Erhöhung der Privilegien für Systemzugang
Ausnützung einer Sicherheitslücke, Passwörter finden
Common Attacks
Threat, carried out by an intruder = attack.
- Accessing and reading memory
- Unauthorized System Calls
- Authorized calls with unauthorized parameters
-
Using escape keys
(
DEL,BREAK, ...)
- Socaial engineering, phishing, black-mailing
zB Stack/Buffer Overflow Attack
Buffer überschreiben, return adresse zu Stack-Anfang überschreiben wo NoOps und anschließend der Exploit-Code steht.
Intrusion Detection
Threshold detection zB Anzahl der Loginversuche
Anomaly Detection Heuristiken um Anomalien zu finden (nicht verlässlich)
Zugriffsmustern vergleichen mit "typischen" Zugriffsmustern von Accounts/Benutzern
Audit records Logging von Operationen, Involvierte, Aktion, Resource Usage, Zeit, ...
Malware
Virus repliziert sich selbst, zB Key Logger oder DOS durch Ressourcenblockierung
Worm repliziert und verschickt sich selbst in einem Netz zB via mail, remote login
Trojan Horse versteckter Code in vermeintlich gutem Programm
Logic Bomb Aktiviert sich selbst bei bestimmter Bedingung, zb Zeitablauf
Trapdoor Geheimer weg Zugriffskontrolle zu bypassen
Port Scan automatisierter Port scan, scripts für common vulnerabilities ausführen
Denial of Service Überlastung eines Rechners
DDoS Distributed Denial of Service, gleichzeitig mit mehreren Rechnern
____________
Password Authentication
Salt
Speicherplatz beschränkt, aber wir wollen möglichst viele Zeichenkombinationen
Es wird unverschlüsselt der hash
h(salt ++ password)
gespeichert.
Countermeasures against Dictionary Attacks
- One-time Password (transaction authentication number TAN)
- Zeitablauf von Passwörtern
- Challenge Response Protokolle (Verschlüsselung)
- timeout between guesses, locking account
- Logging, showing last time user logged in
Access Control
Protection in OS: Zugriffkontrolle von user / user processes.
Identification the ID you claim to have
Authentication proving your ID, to get a premission, get authrorized
Authenticity successful authentication
Credentials evidence used to prove your ID
Accountability ability to trace actions back to entities in a system (requires traceability)
Protokollierung in Security Audit records.
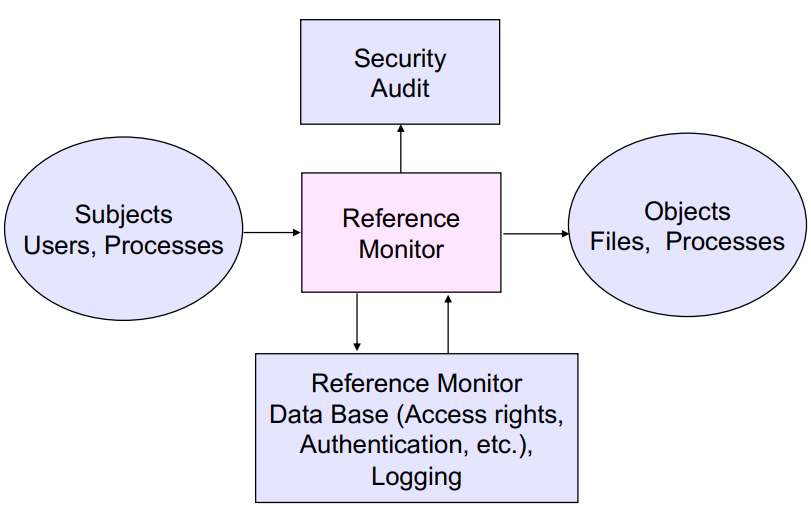
Mechanismus Implementierung in OS, sichert Policy-Einhaltung zB mit Access Matrix
(Security-)Policy von Benutzer bestimmt
Protection Domains
Role / Group / Domain Based Access Control
Role = Set of users (like Administrator, PowerUser, Users, Guest)
Each role has its own domain = set of access-rights (pairs of objects, rights)
In unix the domain / role of each process is defined through IDs
(UID,GID)
.
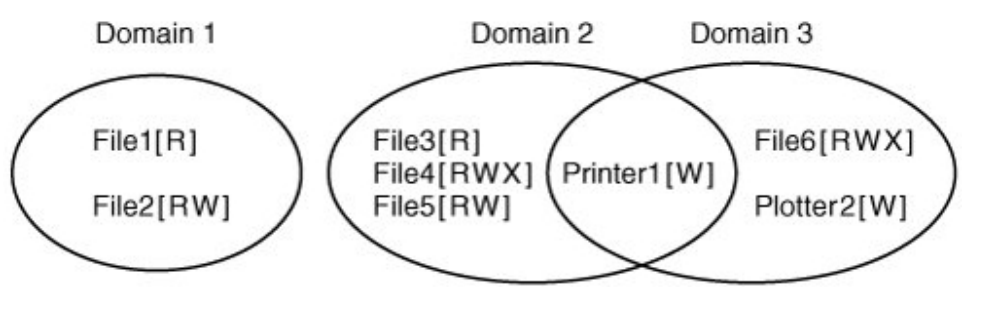
Access Control Matrix
(Domain Object) Access rights read, write, execute
Dynamic Protection
Allows changing access rights in matrix
Has special access rights for owner
Transfer: changing the role / domain of a process allowed
Transfer security policy stored in (ObjectObject)Transfer rightschange, dont change
Access Control List ACL(object centered)
list: subjects access rights of each file
- identification required
- delegation: asking admin to add node
- revocation: modifying nodes (easy)
Token / Capability List(subject centered)
list: unforgable tokens of each process
- identification not required
- delegation: passing token (easy)
- revocation: only with extra bookkeeping
Lock-Key System
Each object has an unforgable set of locks (bit-patterns).
Each domain has an unforgable set of keys (bit-patterns).
The key of the process' domain must match with that of the object.
____________
Bell and LaPadula’s Model
Rules for Information-Flow
Security Classification Hierarchie für Subjects und Objects (zB top secret, secret, public)
Goal: Data Confidentiality (not leaking classified information to unclassified files)
Actions: Operationen von Subjects auf Objects:
read-only no modifications
append writing without reading
execute without reading or writing
read-write
Security Axioms
-
Simple security property
Read"no read up"
-
The *property (star property)
Append"no write down"
Read und Write
Beispiel
Bedeutet Subject kann Object lesen und schreiben